Cyberattacks are constantly growing. They are becoming more advanced and aggressive by the day, making it more difficult to protect the data.
There are various types of cyberattacks. Some forms of attacks are more harmful than others, but every form poses a certain and unavoidable business risk. Here are few scary statistics:
- According to the University of Maryland, hackers attack every 39 seconds, on an average 2,244 times a day.
- A low-end cyberattack returns around $25,000 to the creators, while high-end ones return almost $1 million per month, estimates Deloitte.
- According to IBM 2019 Cost of a Data Breach report, it takes 279 days globally to identify and contain a data breach.
The potential damage from a cybersecurity incident can be enormous and disastrous to your business. Hence, to avoid becoming a victim of a cyberattack, it is important to have a cybersecurity plan in place.
As the proverb goes, “Hope for the best, but prepare for the worst.” This is all the more true in case of cyberattacks and this article will arm you with information about 15 types of cyberattacks every business needs to be aware of.
Let’s start with the basics:
What is a cyberattack?
A cyberattack is a digital or online attack on a system, organization or an individual aimed to steal, corrupt or disrupt the assets (digital assets, digital services, or physical components).
Bad actors launch different types of cyberattacks to breach sensitive information (related to personal, financial details), disrupt the operations, steal money, or damage the reputation of a company or an individual.
Related Read: Top 10 cybersecurity incidents in 2020
What are the different types of cyberattacks?
#1 Phishing
Phishing is the biggest and most damaging among all types of cyberattacks that small businesses are facing today. It accounts for 90% of the total data breaches and nearly 1.5 million new phishing sites are created each month, according to a report.
Phishing attacks happen when an attacker uses social engineering to look like a trusted contact. The attacker tempts a user to download an infected file or click on a malicious link to get access to critical information of the user.
Over the years, phishing attacks have become more sophisticated, with hackers using different ways to convince users by pretending to be genuine business contacts. There has been a rise in hackers stealing credentials from top-level executives of organizations and using them fraudulently to request payments from employees.
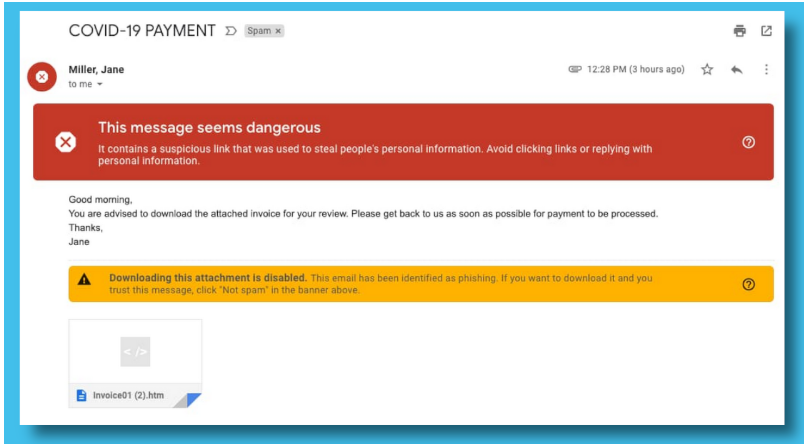
Recently, there has been an increase in the phishing scams relating to COVID-19. Read about how to avoid phishing attacks.
#2 Distributed Denial of Service (DDoS)
A distributed denial-of-service (DDoS) attack happens when attackers overwhelm a website or computer system with too much traffic from different IP addresses. As a result, the business system becomes unavailable. Such attacks are commonly used against large organizations.
The aim is to make the business’ websites and services inoperable. Hackers use this technique to divert the attention of the organization. While the organization tries to restore its services, the attackers may pursue to break into its system and steal the information.
DDoS attacks are one of the most powerful weapons online, with 16 attacks taking place every 60 seconds. Some examples of DDoS attacks include UDP flood attack, SYN flood attack, and DNS amplification.
You should take steps to protect your business from DDoS attacks. Develop a DDoS attack prevention plan to ensure business continuity.
#3 SQL Injection
An SQL (Structured Query Language) injection occurs when a cybercriminal inserts malicious code into an SQL database. As a result, the SQL server automatically exposes sensitive data from the database.
This attack can be executed by simply typing a malicious code into an input field such as a website’s search box. Through an SQL injection, an attacker can read, modify or remove data, or even run an administrative command to shut down your whole database.
Organizations must ensure network security regularly. Additionally, to minimize the risks, they need to use a web application firewall (WAF) as protection against SQL injection.
#4 Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) attack is a type of injection in which an attacker injects malicious codes into otherwise trusted websites. XSS cyberattacks occur when a cybercriminal sends malicious scripts using a web application and that malicious script is added within a dynamic content that is delivered to a victim’s browser.
XSS attacks are common on web pages that allow comments. For example, an attacker posts a comment containing malicious code wrapped in <script>…</script> tags. The web server shows the following comment with code to users that visit the website. Once the victim loads the website, the attacker’s malicious codes execute.
When the script is executed, the attacker can monitor the victim’s keystrokes to access critical data.
#5 Malware
A malware is a malicious software. A malware attack happens when attackers create malicious software that is downloaded on someone else’s computer without their knowledge, in order to get unauthorized access to the user’s sensitive information, or damage the system, to take revenge or for financial gains.
There are various types of malware attacks, for example, viruses, worms, keyloggers, and spyware. According to Accenture, malware stands as the most expensive cyberattack, costing victims up to $2.6 million.
Organizations can minimize the consequences and prevent such attacks by using a cybersecurity solution that can scan and identify malware instantly.
#6 Ransomware
Ransomware is a kind of malicious software. Hackers install malicious software in the user’s device to gain access to the files or systems and block user from accessing those files or systems. Then, the whole system or files are seized using encryption until the victim pays money (ransom) in exchange for the decryption key.

Ransomware attacks are one of the most prevalent ones among all sectors. If you fall victim to a ransomware attack, the best way to restore your impacted files is by using a good backup solution so that you can regain access to your data as fast as possible.
Check DSCI-PwC report on how to prevent ransomware attacks in 2020.
#7 Spyware
Spyware is a type of software that spies on the internet activity and steals sensitive information of an individual or a company. It collects your personal information and shares it with data firms, advertisers, or the public. Hackers can also change user configuration settings of your device. So, it is important to use a strong password and keep your devices updated.
#8 Man in the middle (MITM) attack
A man-in-the-middle attack (MITM) is one of the sneakiest of all types of cyberattacks. It occurs when an attacker secretly eavesdrops or alters communication between two parties who believe they are talking directly with each other. Attackers can also steal login or password details, or personal information or even corrupt the data.
Man in the middle attacks mostly happen when you are using an open wi-fi connection, for example, in hotels or malls where users are offered free wi-fi connection, and thus, attackers can easily invade your session.
You need to include multi-factor authentication and maximize network control to prevent MITM attacks. Another best way to authenticate communication is by using encryption protocols like SSL or TLS.
#9 Insider threats
Insider threat is considered as the biggest contributor to cyberattacks. An insider threat is a malicious threat that begins within the targeted organization. This involves an existing or a former employee or any business associate who has access to the organizational information and misuses it, intentionally or unintentionally.
Most of the insider attacks happen by mistake or as a result of negligence. The best way to prevent such cyberattacks is by training the employees on security awareness.
#10 Advanced Persistent Threats (APT)
An advanced persistent threat (APT) is a targeted cyberattack where an attacker gains unauthorized access to a network or system and remains there for an extended period of time, without being detected. APTs are particularly dangerous for organizations as attackers have access to sensitive information for a very long time.
APT attacks are aimed to steal or spy an organization’s sensitive data rather than damaging them. Such threat actors typically target large corporations in sectors like the manufacturing industry, national defense, and the banking industry. This is because these industries deal with high value information, involving intellectual property, financial data, military plans, government data, and enterprise data.
APT attacks are often difficult to detect so organizations of all sizes must implement robust security measures to quickly detect and respond to these threats.
#11 Zero-day
A zero-day is a software security flaw that is left unpatched by the organization and can be exploited by the attackers for their benefit.
A zero-day exploit can include malware or unauthorized access to user information. This can further embed malicious code into your software or even steal your data. Users can prevent such types of cyberattacks by keeping their software and security patches updated or install security software to block unknown threats.
#12 Birthday attack
A birthday attack is a type of cryptographic cyberattack, which is performed to crash the hash algorithms used to verify the integrity of software, message or e-signature. A birthday attacker focuses on disrupting the communication between people, groups or entities.
For example, if in case there’s a vulnerability in the electronic signature and the attacker gets access to this, then that attacker can attach a victim’s digital signature to a malicious contract. To avoid birthday attacks, users must use lengthy and a different hash algorithm each time.
#13 IP Spoofing
IP spoofing is a type of cyberattack where an attacker creates IP address packets with a false address to either hide the sender’s identity or to represent as another computer system, or both. Once the user accepts the address packets, the hacker can take control of the user’s computer sessions. Further, the hacker can flood the victim’s network with traffic, or cause disruption and crashing.
To protect against IP spoofing, you can monitor networks for suspicious activity, deploy packet filtering, and use strong verification methods.
#14 Drive-by download attacks
Drive-by download attacks refer to malicious programs like malware, spyware, and adware that get installed on your computer or device, without your knowledge. Drive-by downloads may occur when you click on an email attachment, a link, website, or even press a download button.
For example, if a user visits a website that contains malicious content, then that malicious content can exploit the browser’s vulnerabilities and then run the malicious code without the user’s consent. This way the user may become a victim of drive-by download cyberattack.
You can prevent drive-by download attacks by installing antivirus software and keeping your system updated.
#15 Macro Virus
A macro virus is a computer virus that is written in the macro language (a programming language that can be embedded into applications like Word, Excel, etc.).
Once a macro virus is embedded into a software application, it will hijack or take control of the application’s commands, or even spread itself to infect other applications and the network. It can also damage the computer or device permanently or steal the victim’s personal information.
Organizations must use a reliable security solution to prevent macro viruses.
Fighting back – how to prevent cyberattacks?
The answer is simple – Be prepared!
Fortunately, there are simple yet effective methods to safeguard your business and data from different types of cyberattacks. A single cyberprotection solution by Acronis can help fulfil all your needs. It is world’s first Complete Cyber Protection Solution that integrates backup, disaster recovery, AI-based malware protection and cybersecurity.
Share your feedback and queries in the comments section.
Read Next: Ransomware and Viruses: Top differences you should know



Hi
I read the full article and found it very informative. Getting a chance to know the types of cyber attacks helps to stay safe from such type of attacks or spams.
Very informative.