Mobile devices have become deeply integrated into our daily lives. We rely on smartphones and tablets for everything from communication to entertainment, shopping to banking, and more. However, with great convenience comes significant risk. As these devices store more of our personal and financial data, they have become a prime target for cybercriminals.
Managing mobile device security is becoming increasingly challenging as mobile malware attacks continue to rise. Kaspersky detected 6.7 million mobile attacks in the third quarter of 2024 alone, highlighting the growing threat landscape.
In this blog, we will explore the top 10 mobile security threats that users face in 2025 along with simple yet effective mobile security tips 2025 to mitigate these risks. By understanding the latest mobile threats landscape and learning defensive tactics, you can protect your device and data from attacks.
Top Mobile Security Threats in 2025
1. Ransomware Attacks
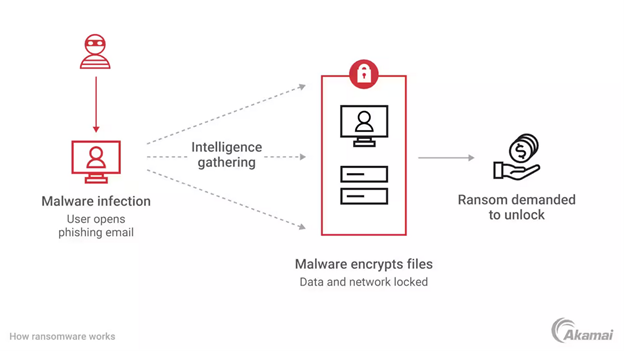
Ransomware remains a severe threat with strain variants capable of encrypting data and locking mobile devices until a ransom is paid. Over 90% of mobile users worldwide have internet-enabled smartphones, making them ransomware targets. Most worryingly, many ransomware apps now disguise themselves as innocent games or utilities, deceiving unsuspecting users into downloading them.
How to stay protected: Use a mobile security app to block suspicious apps. Back up data regularly so your information can be restored without paying ransoms.
2. Data Breaches
Data breaches through hacking or malware lead to customer data leaks. Once cyber criminals access a device, all the personal and financial information is compromised. Even more alarming is many users are unaware their data has been stolen for months or even years.
How to stay protected: Use strong passwords, VPNs, trusted Wi-Fi networks and limit sharing of sensitive data online.
3. Fake Apps and Downloads
Filled with enticing games, utilities, wallpapers and more – app stores remain a hotspot to lure victims into downloading fake apps hiding malware. From stealing contacts to monitoring calls, these fraudulent apps are a launch pad for identity theft and financial fraud.
How to stay protected: Vet app developers, check reviews thoroughly, avoid unnecessary app permissions and installations from outside the official app stores.
4. Social Engineering
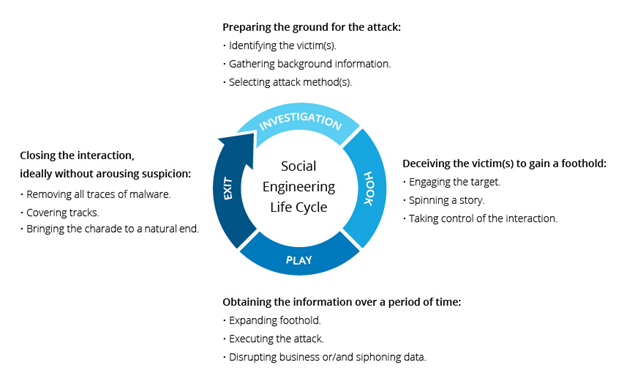
Also called ‘human hacking’, social engineering aims to manipulate users into sharing sensitive data or performing dangerous actions. From personalized phishing attempts to fake customer calls, hackers employ psychological tricks and emotional appeals to successfully breach defenses. With personal data floating online, the schemes seem authentic and even tech-savvy folks get duped.
How to stay protected: Verify requests over other communication channels before acting, no matter how urgent the plea. Limit sharing personal information publicly that can assist in crafting targeted social engineering attacks.
5. Risky Wi-Fi Networks
Public Wi-Fi networks, like those in cafes or airports, remain a hot zone for hacker activity. Unsecured networks make it easy to steal usernames, passwords, track browsing activity and implant malware.
How to stay protected: Avoid logging into sensitive accounts over public Wi-Fi. Use safe mobile browsing and trusted VPNs that encrypt data.
6. Unauthorized Access
Weak passwords and reused passwords across other sites make getting access to user accounts a cakewalk. By not using multi-factor authentication for mobile access, most accounts can be accessed with just the username and password.
How to stay protected: Create unique complex passwords for mobile access. Enable multi-factor authentication across email, social media and financial accounts.
7. Phishing Sites and Emails
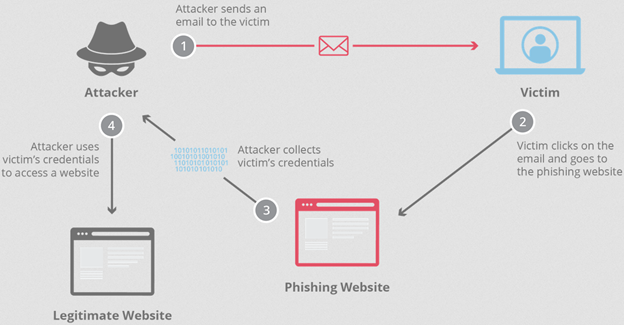
Phishing ploys now go beyond spammy emails to encrypted messaging apps, legitimate-looking websites and even phone calls. Adopting familiar branding and urgent tones, users get manipulated into clicking dangerous links, downloading malware payloads or revealing account details that lead to financial theft and identity spoofing.
How to stay protected: Carefully inspect links and sender details before clicking or sharing data. Avoid opening links from unknown senders.
8. Spyware Infections
Spyware infections can reach your mobile through fake apps and compromised sites. Once installed, it can secretly record calls, texts, track locations, and access device data. Spyware now comes fully loaded with capabilities to turn on cameras and microphones without being detected.
How to stay protected: Vet and limit app permissions. Use anti-malware apps to detect spyware infections. Avoid clicking random pop-ups and messages.
9. SIM Swapping
Though not widespread yet, SIM swapping has emerged as a new hack where fraudsters socially engineer mobile company staff into issuing replacement SIM cards. With control of the target’s phone number, hackers can access and empty financial accounts secured through texts or calls.
How to stay protected: Set up account alerts, use 2-factor authentication via authentication apps instead of texts, and limit sharing of phone numbers publicly.
10. Insider Threats
Insider threats can account for mobile security incidents caused by employees, contract staff or business partners misusing access rights. Whether intentional or not, data deletion, theft and unauthorized access from trusted insiders makes detection harder but damages just as severe.
How to stay protected: Use enterprise mobile management tools to limit access and permissions based on user roles. Monitor account activity for irregular patterns consistent with insider misuse. Enforce separation of duties and mandatory access reviews.
Adopting Mobile Security Best Practices
While the mobile threat landscape may seem daunting, following best practices consistently can significantly reduce risks. Start with the essentials—use strong passwords, enable biometrics, update software regularly, back up data, and install only trusted apps. Take security a step further by using a VPN on public Wi-Fi, deploying anti-malware apps, and avoiding jailbreaking your devices. Stay vigilant—verify requests, limit online information sharing, and report suspicious activity promptly. Most importantly, invest in a robust cyber protection solution to safeguard your data against ransomware and evolving threats.
Secure Your Mobile with Acronis Cyber Protect
Keeping your smartphone data secure has never been easier! Acronis Cyber Protect Home Office is an all-in-one solution to safeguard data across Windows PCs, Macs, iPhones, iPads, and Android devices. Enjoy seamless automatic backups to your PC, NAS, or Mac the moment your device connects to Wi-Fi. Ensure your valuable data is protected with Acronis Cyber Protect—available now at ZNetLive!
Read next: Acronis Cyber Protect Cloud vs Veeam: Which backup solution is right for you?


